I’ve received this email:
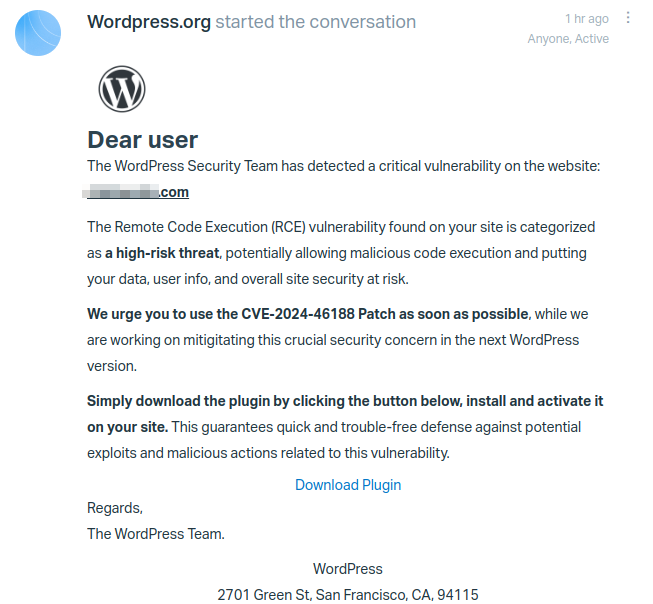
If you follow the link to phishing URL https://us.en-wordpress.org/plugins/cve-2024-46188/, download the file, and analyze the code, you immediately realize that this plugin is malicious and does the following:
- it creates an admin user, where the username is a function of the website URL on which the plugin is installed, and the password is deterministic (E5rLDmno9F), although obtained by shuffling a string;
- it makes that user unsearchable from the WP interface;
- it makes the plugin unsearchable from the WP interface;
- it pings home (https://defcve.com/wpapi?siteurl=, again some shuffling happens to hide this) to let the scammers know when someone “bites”;
- it downloads P.A.S. fork from home and saves it to disk.
Pretending to be the Red Cross to perform a sneak attack is one of the vilest things a human being can do. Stay safe, kids, always be paranoid and never trust a famous logo.
Post a Comment through Mastodon
If you have a Mastodon account, .